Regularly changing sign-in options (i.e. PIN, user password and picture password) makes sense in terms of password protection and data safety. In consequence, this article illustrates how to change sign-in options on Windows 10 computer in detail.
- 1password Sign In To Chrome
- One Password Sign In
- Sign In To 1password
- Sign In 1password Ipad
- 1password Sign In Address Change
If you already know your current password and want to change it. Select Start Settings Accounts Sign-in options.Under Password, select the Change button and follow the steps. Reset your Windows 10 local account password. If you've forgotten or lost your Windows 10 password for a local account and need to sign back in to your device, the below options might help you get up and running. Yahoo makes it easy to enjoy what matters most in your world. Best in class Yahoo Mail, breaking local, national and global news, finance, sports, music, movies and more.
Sign in to your account on 1Password.com. Select the Login item for the website and click Edit. Click 'label' in a new section, and enter 'One-time password'. Click to the right of the field and choose One-Time Password. On the website, choose to enter the code manually. Copy the code, then paste it in the One-Time Password field. Sign in - Google Accounts. Review our team pricing and sign up for a Free Trial to get access to password manager, digital vault, password generator, digital wallet, and more.
Part 1: Change user password on Windows 10
Step 1: Enter PC settings.
Step 2: Select Users and accounts.
Step 3: Open Sign-in options and tap the Change button under Password.
Step 4: Enter current user password and tap Next.
Step 5: Type a new password, re-type it, input password hint and click Next.
Step 6: Choose Finish to complete changing user password.
Tip: You can also change your user password in the Control Panel, following the process below.
Control Panel/User Accounts and Family Safety/User Accounts/Manage another account/Select a user/Change the Password
Part 2: Chang picture password on Windows 10
Step 1: Access PC settings and open Users and accounts.
Step 2: Select Sign-in options and click the Change button under Picture password.
Step 3: Type user password and tap OK to confirm your account info.
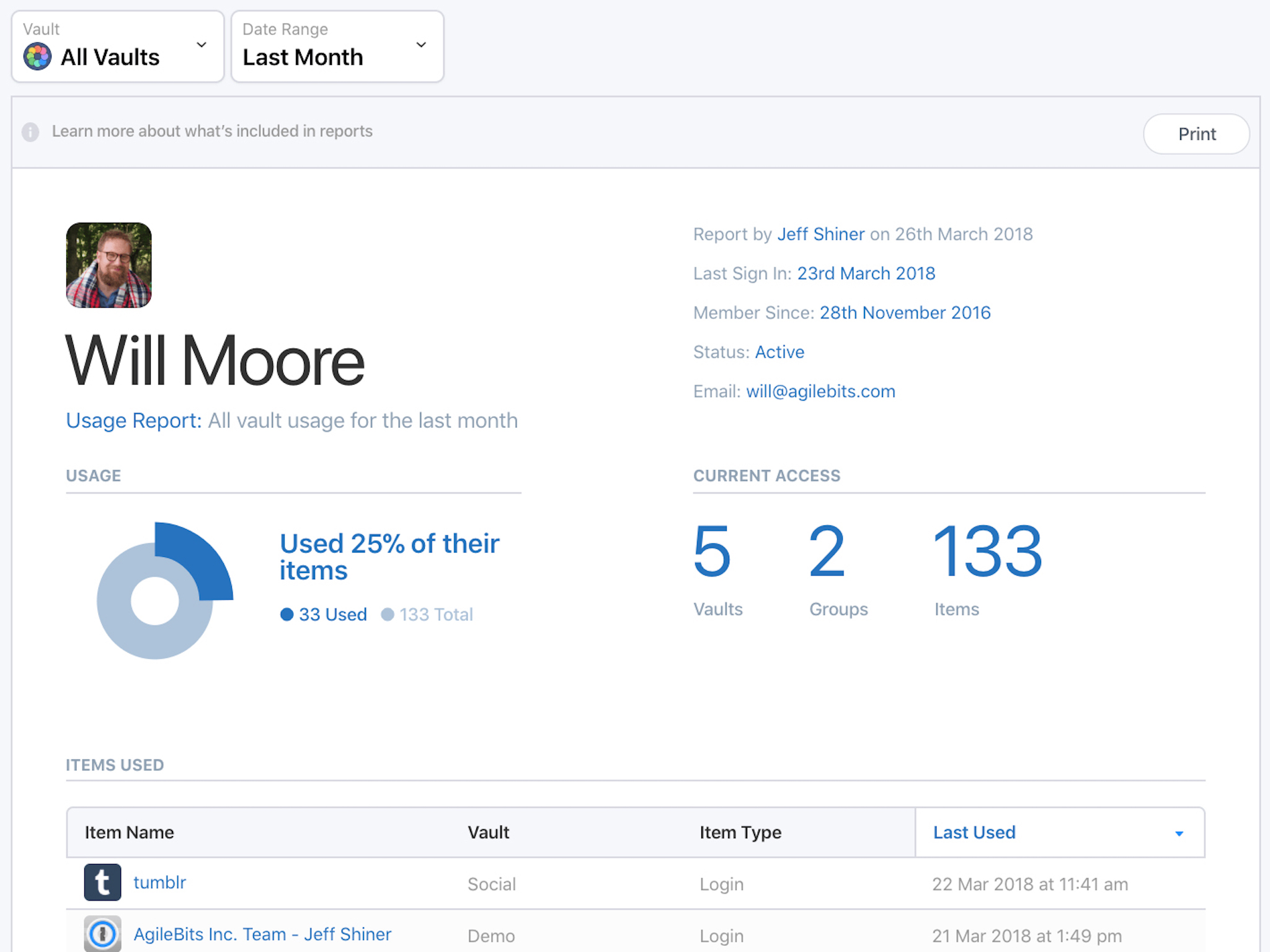
Step 4: Select Use this picture to continue.
Step 5: Draw three new gestures (e.g. circles, straight lines and taps) on the picture.
Step 6: Redraw the three gestures on the picture.
Step 7: Tap Finish to exit.
Part 3: Chang PIN on Windows 10
Step 1: Open PC settings and enter Users and accounts.
Step 2: Choose Sign-in options and tap the Change button under PIN.
Step 3: Input user password and click OK to go on.
Step 4: Enter a new PIN containing 4 digits, reenter it and select Finish.
Related Articles:
-->The Microsoft Authenticator app can be used to sign in to any Azure AD account without using a password. Microsoft Authenticator uses key-based authentication to enable a user credential that is tied to a device, where the device uses a PIN or biometric. Windows Hello for Business uses a similar technology.
This authentication technology can be used on any device platform, including mobile. This technology can also be used with any app or website that integrates with Microsoft Authentication Libraries.
People who enabled phone sign-in from the Microsoft Authenticator app see a message that asks them to tap a number in their app. No username or password is asked for. To complete the sign-in process in the app, a user must next take the following actions:
- Match the number.
- Choose Approve.
- Provide their PIN or biometric.
Prerequisites
To use passwordless phone sign-in with the Microsoft Authenticator app, the following prerequisites must be met:
- Azure AD Multi-Factor Authentication, with push notifications allowed as a verification method.
- Latest version of Microsoft Authenticator installed on devices running iOS 8.0 or greater, or Android 6.0 or greater.
- The device on which the Microsoft Authenticator app is installed must be registered within the Azure AD tenant to an individual user.
Note
If you enabled Microsoft Authenticator passwordless sign-in using Azure AD PowerShell, it was enabled for your entire directory. If you enable using this new method, it supercedes the PowerShell policy. We recommend you enable for all users in your tenant via the new Authentication Methods menu, otherwise users not in the new policy are no longer be able to sign in without a password.
Enable passwordless authentication methods
To use passwordless authentication in Azure AD, first enable the combined registration experience, then enable users for the password less method.
Enable the combined registration experience
Registration features for passwordless authentication methods rely on the combined registration feature. To let users complete the combined registration themselves, follow the steps to enable combined security information registration.
Enable passwordless phone sign-in authentication methods
Azure AD lets you choose which authentication methods can be used during the sign-in process. Users then register for the methods they'd like to use.
To enable the authentication method for passwordless phone sign-in, complete the following steps:
- Sign in to the Azure portal with a global administrator account.
- Search for and select Azure Active Directory, then browse to Security > Authentication methods > Policies.
- Under Microsoft Authenticator, choose the following options:
- Enable - Yes or No
- Target - All users or Select users
- Each added group or user is enabled by default to use Microsoft Authenticator in both passwordless and push notification modes ('Any' mode). To change this, for each row:
- Browse to ... > Configure.
- For Authentication mode - Any, Passwordless, or Push
- To apply the new policy, select Save.
User registration and management of Microsoft Authenticator
Users register themselves for the passwordless authentication method of Azure AD by using the following steps:
- Browse to https://aka.ms/mysecurityinfo.
- Sign in, then add the Authenticator app by selecting Add method > Authenticator app, then Add.
- Follow the instructions to install and configure the Microsoft Authenticator app on your device.
- Select Done to complete Authenticator configuration.
- In Microsoft Authenticator, choose Enable phone sign-in from the drop-down menu for the account registered.
- Follow the instructions in the app to finish registering the account for passwordless phone sign-in.
An organization can direct its users to sign in with their phones, without using a password. For further assistance configuring the Microsoft Authenticator app and enabling phone sign-in, see Sign in to your accounts using the Microsoft Authenticator app.

Step 4: Select Use this picture to continue.
Step 5: Draw three new gestures (e.g. circles, straight lines and taps) on the picture.
Step 6: Redraw the three gestures on the picture.
Step 7: Tap Finish to exit.
Part 3: Chang PIN on Windows 10
Step 1: Open PC settings and enter Users and accounts.
Step 2: Choose Sign-in options and tap the Change button under PIN.
Step 3: Input user password and click OK to go on.
Step 4: Enter a new PIN containing 4 digits, reenter it and select Finish.
Related Articles:
-->The Microsoft Authenticator app can be used to sign in to any Azure AD account without using a password. Microsoft Authenticator uses key-based authentication to enable a user credential that is tied to a device, where the device uses a PIN or biometric. Windows Hello for Business uses a similar technology.
This authentication technology can be used on any device platform, including mobile. This technology can also be used with any app or website that integrates with Microsoft Authentication Libraries.
People who enabled phone sign-in from the Microsoft Authenticator app see a message that asks them to tap a number in their app. No username or password is asked for. To complete the sign-in process in the app, a user must next take the following actions:
- Match the number.
- Choose Approve.
- Provide their PIN or biometric.
Prerequisites
To use passwordless phone sign-in with the Microsoft Authenticator app, the following prerequisites must be met:
- Azure AD Multi-Factor Authentication, with push notifications allowed as a verification method.
- Latest version of Microsoft Authenticator installed on devices running iOS 8.0 or greater, or Android 6.0 or greater.
- The device on which the Microsoft Authenticator app is installed must be registered within the Azure AD tenant to an individual user.
Note
If you enabled Microsoft Authenticator passwordless sign-in using Azure AD PowerShell, it was enabled for your entire directory. If you enable using this new method, it supercedes the PowerShell policy. We recommend you enable for all users in your tenant via the new Authentication Methods menu, otherwise users not in the new policy are no longer be able to sign in without a password.
Enable passwordless authentication methods
To use passwordless authentication in Azure AD, first enable the combined registration experience, then enable users for the password less method.
Enable the combined registration experience
Registration features for passwordless authentication methods rely on the combined registration feature. To let users complete the combined registration themselves, follow the steps to enable combined security information registration.
Enable passwordless phone sign-in authentication methods
Azure AD lets you choose which authentication methods can be used during the sign-in process. Users then register for the methods they'd like to use.
To enable the authentication method for passwordless phone sign-in, complete the following steps:
- Sign in to the Azure portal with a global administrator account.
- Search for and select Azure Active Directory, then browse to Security > Authentication methods > Policies.
- Under Microsoft Authenticator, choose the following options:
- Enable - Yes or No
- Target - All users or Select users
- Each added group or user is enabled by default to use Microsoft Authenticator in both passwordless and push notification modes ('Any' mode). To change this, for each row:
- Browse to ... > Configure.
- For Authentication mode - Any, Passwordless, or Push
- To apply the new policy, select Save.
User registration and management of Microsoft Authenticator
Users register themselves for the passwordless authentication method of Azure AD by using the following steps:
- Browse to https://aka.ms/mysecurityinfo.
- Sign in, then add the Authenticator app by selecting Add method > Authenticator app, then Add.
- Follow the instructions to install and configure the Microsoft Authenticator app on your device.
- Select Done to complete Authenticator configuration.
- In Microsoft Authenticator, choose Enable phone sign-in from the drop-down menu for the account registered.
- Follow the instructions in the app to finish registering the account for passwordless phone sign-in.
An organization can direct its users to sign in with their phones, without using a password. For further assistance configuring the Microsoft Authenticator app and enabling phone sign-in, see Sign in to your accounts using the Microsoft Authenticator app.
Note
Users who aren't allowed by policy to use phone sign-in are no longer able to enable it within the Microsoft Authenticator app.
Sign in with passwordless credential
A user can start to utilize passwordless sign-in after all the following actions are completed:
1password Sign In To Chrome
- An admin has enabled the user's tenant.
- The user has updated her Microsoft Authenticator app to enable phone sign-in.
The first time a user starts the phone sign-in process, the user performs the following steps:
- Enters her name at the sign-in page.
- Selects Next.
- If necessary, selects Other ways to sign in.
- Selects Approve a request on my Microsoft Authenticator app.
The user is then presented with a number. The app prompts the user to authenticate by selecting the appropriate number, instead of by entering a password.
After the user has utilized passwordless phone sign-in, the app continues to guide the user through this method. However, the user will see the option to choose another method.
Known Issues
The following known issues exist.
Not seeing option for passwordless phone sign-in
In one scenario, a user can have an unanswered passwordless phone sign-in verification that is pending. Yet the user might attempt to sign in again. When this happens, the user might see only the option to enter a password.
To resolve this scenario, the following steps can be used:
- Open the Microsoft Authenticator app.
- Respond to any notification prompts.
One Password Sign In
Then the user can continue to utilize passwordless phone sign-in.
Federated Accounts
When a user has enabled any passwordless credential, the Azure AD login process stops using the login_hint. Therefore the process no longer accelerates the user toward a federated login location.
This logic generally prevents a user in a hybrid tenant from being directed to Active Directory Federated Services (AD FS) for sign-in verification. However, the user retains the option of clicking Use your password instead.
Azure MFA server
An end user can be enabled for multi-factor authentication (MFA), through an on-premises Azure MFA server. The user can still create and utilize a single passwordless phone sign-in credential.
If the user attempts to upgrade multiple installations (5+) of the Microsoft Authenticator app with the passwordless phone sign-in credential, this change might result in an error.
Device registration
Before you can create this new strong credential, there are prerequisites. One prerequisite is that the device on which the Microsoft Authenticator app is installed must be registered within the Azure AD tenant to an individual user.
Currently, a device can only be registered in a single tenant. This limit means that only one work or school account in the Microsoft Authenticator app can be enabled for phone sign-in.
Note
Sign In To 1password
Device registration is not the same as device management or mobile device management (MDM). Device registration only associates a device ID and a user ID together, in the Azure AD directory.
Sign In 1password Ipad
Next steps
1password Sign In Address Change
To learn about Azure AD authentication and passwordless methods, see the following articles:

